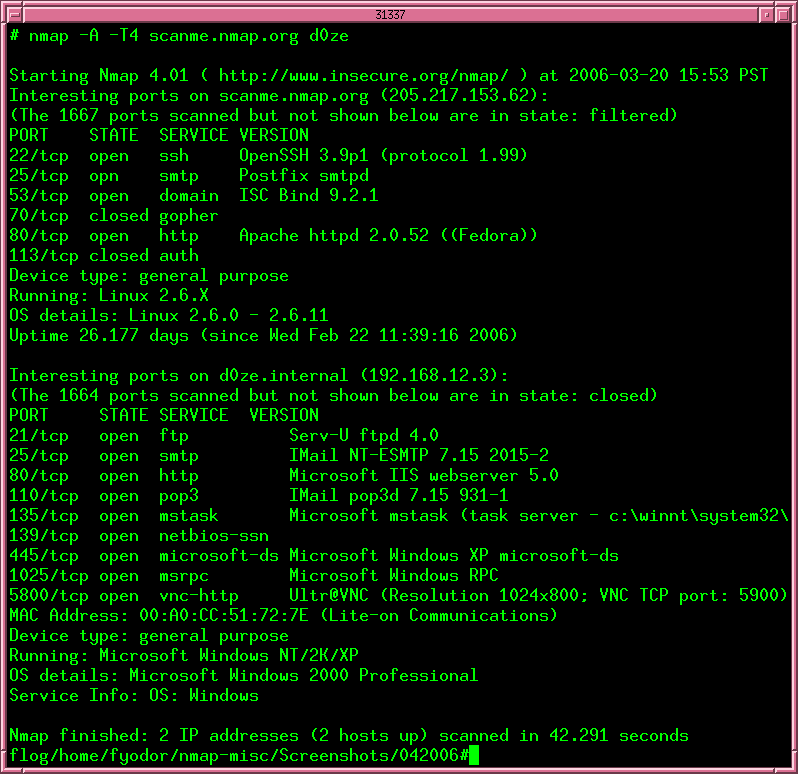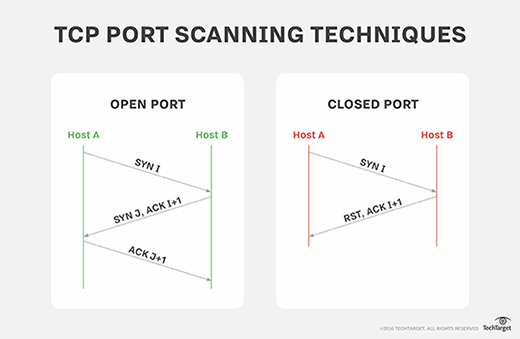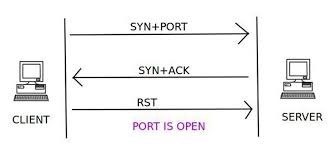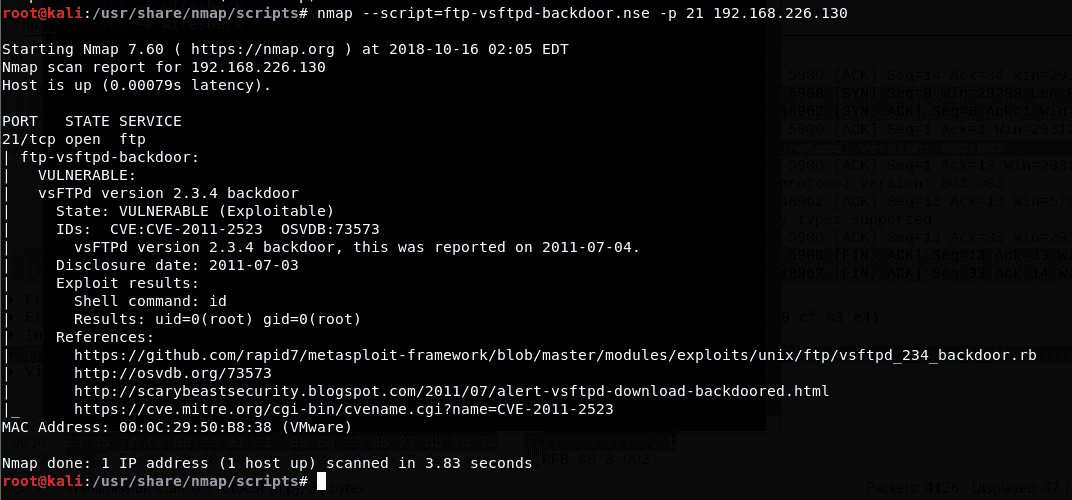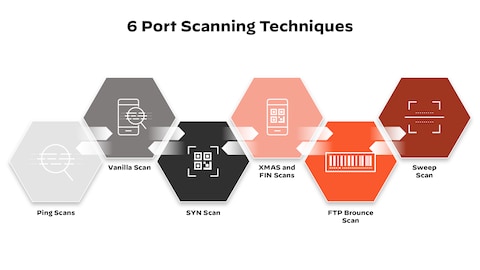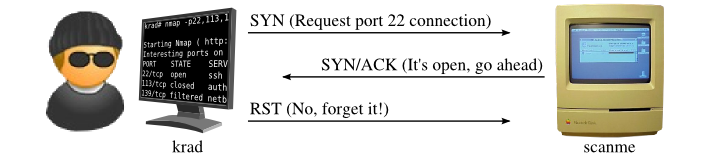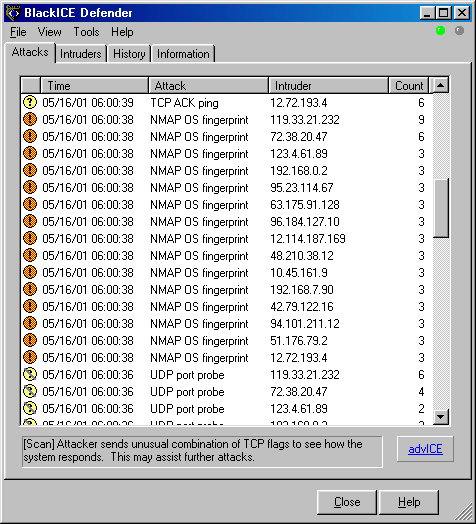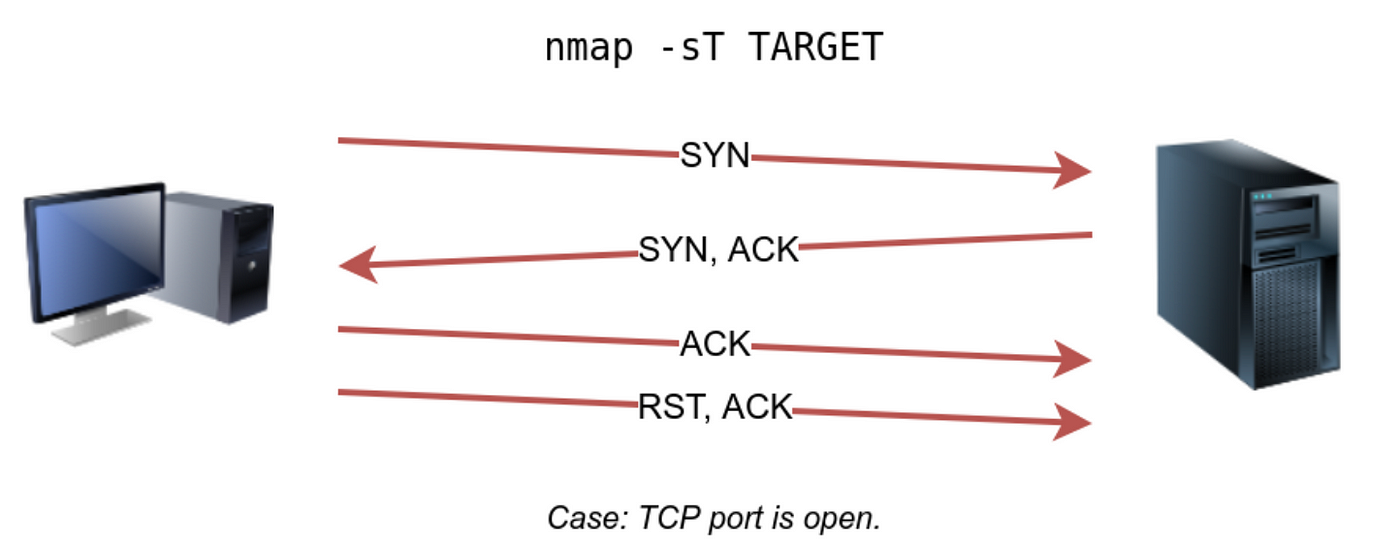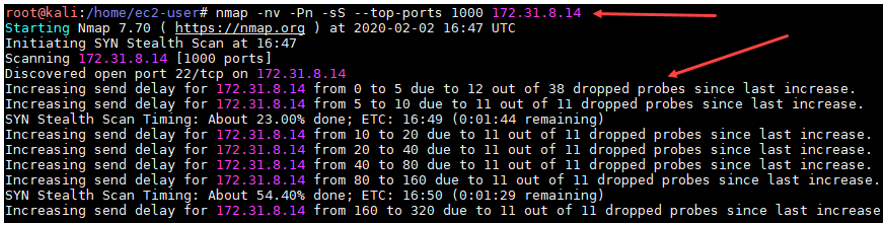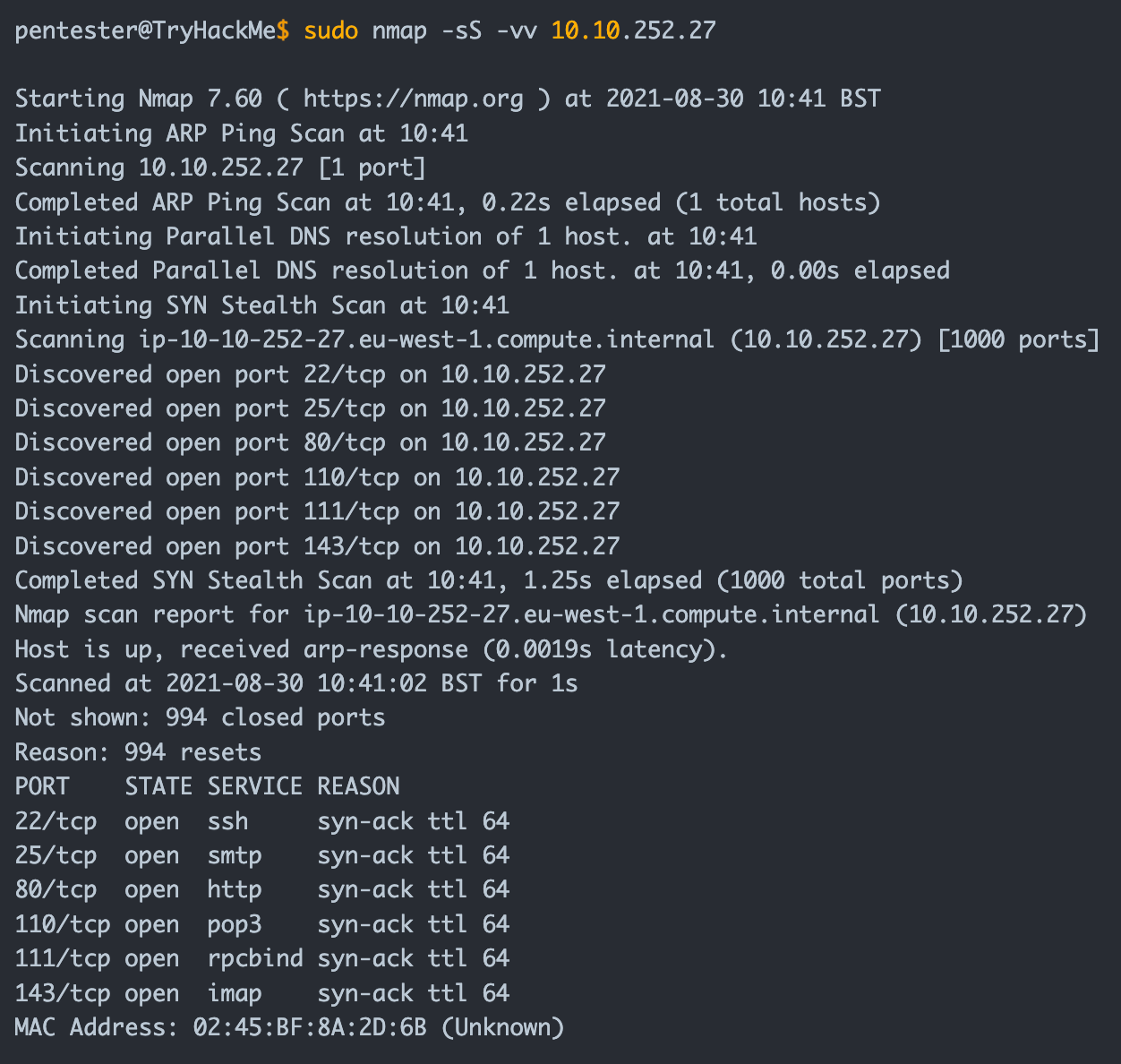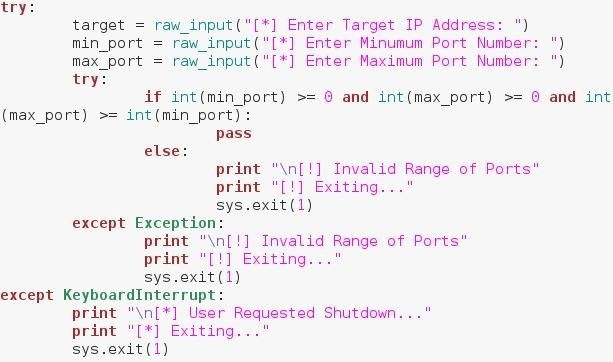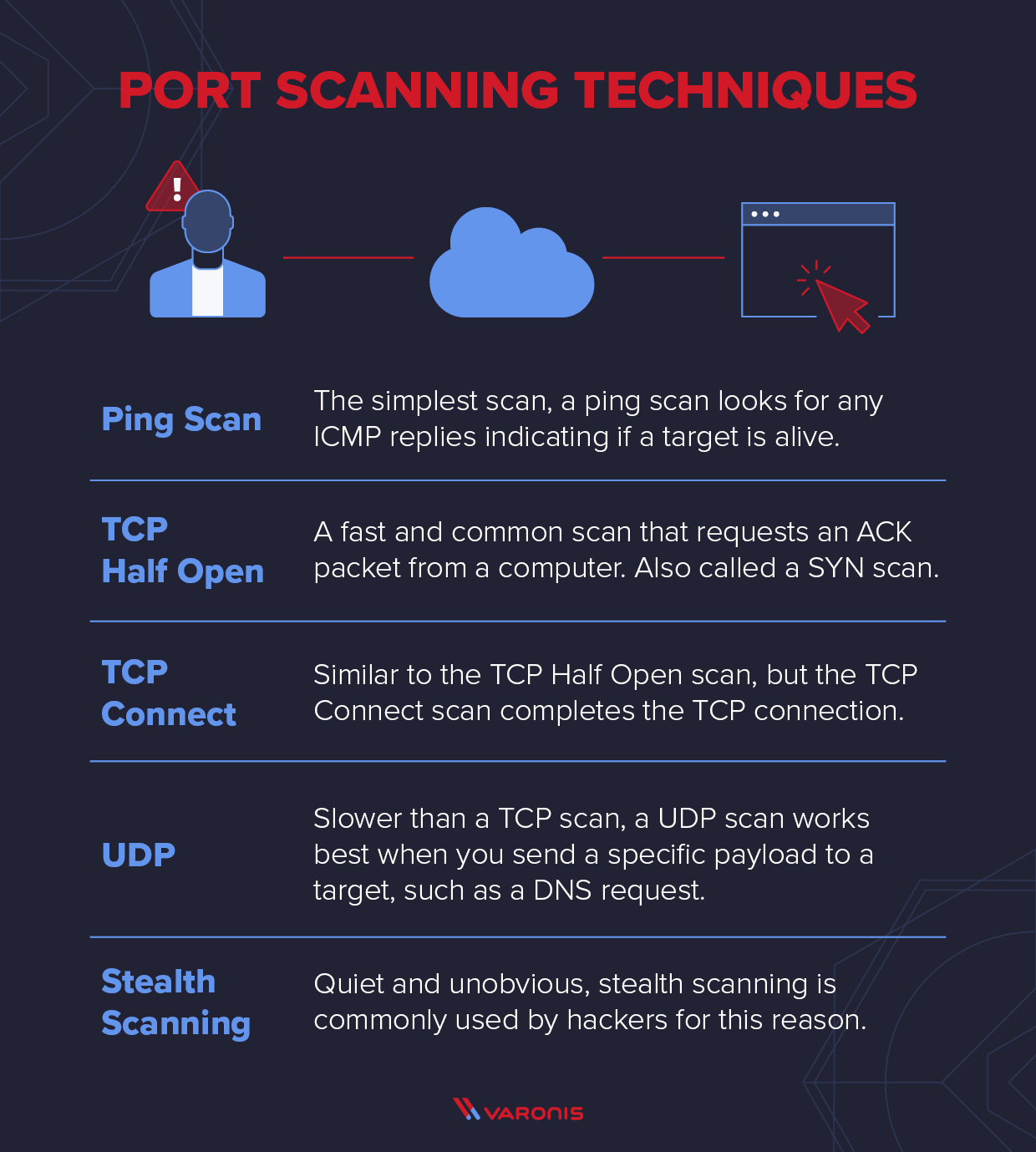
Explaining Port Scanning. A port scan is a common technique… | by Arth Awasthi | FAUN — Developer Community 🐾

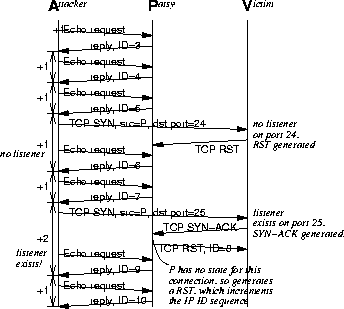
Internet Protocol Identification Number Based Ideal Stealth Port Scan Detection Using Snort | Semantic Scholar

Stealth Port Scan However, if there is a service listening on the port,... | Download Scientific Diagram